下面的系列文章主要围绕《GB/T 38674—2020 信息安全技术 应用软件安全编程指南》进行讲解,该标准是2020年4月28日,由国家市场监督管理总局、国家标准化管理委员会发布,2020年11月01日开始实施。我们对该标准中一些常见的漏洞进行了梳理,大家感兴趣的话可以自己去下载下来学习一下,里面有一些最佳实践是比较好的。
本标准从程序安全和环境安全两个方面提出了提升应用安全性的编程最佳实践。其中,程序安全部分描述软件在资源使用、代码实现、安全功能方面的安全性规范,环境安全部分描述软件的安全管理配置规范。前面的文章为大家讲解了程序安全和代码安全,本文我们针对资源使用安全的网络传输部分进行解读。
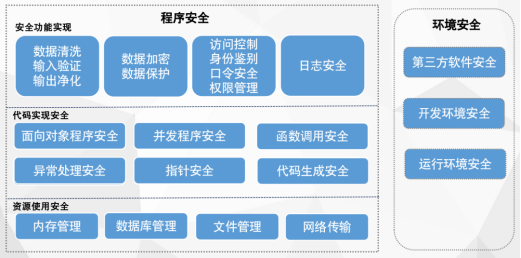
资源使用安全,主要包括:资源管理 、内存管理 、数据库管理 、文件管理 、网络传输这几部分。

【网络传输】
1、使用加密传输确保通信安全
(1)采用加密传输方式保护敏感信息,特别是要求身份鉴别的数据内容,与外部系统交换的数据内容等。
(2)宜使用配合合理的单一标准TLS或SSL对连接保护,并支持对敏感文件或非基于HTTP连接的不连续加密。
(3)避免没有成功的TLS连接后退为一个不安全的连接。
(4)为在TLS连接上传输的cookie设置“安全”属性。
2.会话安全
(1)使用服务器或者框架的会话管理机制,只识别有效的会话标志符。
(2)确保会话标识符的随机性。
(3)建议在账户登出后完全终止相关的会话或连接。
(4)在平衡风险和业务功能需求基础上,最小化会话超时时间。
(5)如果一个会话在登录以前就建立,在成功登录以后,宜关闭该会话并创建一个新的会话。
(6)任何重新进行身份鉴别的过程,宜建议一个新的会话标识。
(7)不允许统一用户ID的并发登录。
网络传输安全主要分为两个方面,一个是传输通道的安全,现在一般都是用HTTPS传输,但是对于一些敏感信息还是需要再次进行加密的。另外一方面就是会话安全,我们在访问一个系统的时候建立一个会话,这个会话怎么来保护它?包括会话的生成机制,怎么生成一个会话,会话使用过程中会话时间是多长,会话超时时间应该怎么设置,会话结束后怎么释放等等都需要考虑。
比如说我们生成一个session,我们登上去以后,要产生一个新的身份标识,我们退出的时候,要让这个session过期。长时间不使用的话要设置一个会话超时时间。
